導入Terraform
前言
前面有稍微提到幾篇是terraform的使用方式,
148. Terraform的基本概念
149. terraform 部署VM,啓動docker安裝metadata_startup_script
183. Terrafrom 建立private cluster
再來把剩下碰到的補一補了。
正文
- 建立完了private cluster,後續要建立SQL 跟 redis的話,該怎麼建?
另外開一個資料夾,重新terraform init,但要注意,
你的backend.hcl是怎麼寫的。
舉例來說,
private cluster的bucket.hcl是這樣
bucket = "terraform-devops"
prefix = "terraform/state"
如果,另一個資料夾裏面的bucket.hcl也相同,
那在產生計劃時,就會把你剛剛建好的private cluster給刪除,
因爲他檢查的是tfstate跟你目前計劃有哪些差別。
所以,需要更改prefix
bucket = "terraform-devops"
prefix = "terraform/other"
這樣在bucket裏面,就會存成兩個不同的tfstate
- terrafrom使用迴圈,減少重複的程式碼
建立兩個bucket,並開啓allUser read
variable "bucket_names" {
type = list(string)
default = ["A-legacy", "B-legacy"]
}
resource "google_storage_bucket" "frontend_bucket" {
uniform_bucket_level_access = true
for_each = { for name in toset(var.bucket_names) : name => name }
name = each.value
force_destroy = false
location = "asia-east1"
storage_class = "STANDARD"
# public_access_prevention = "inherited"
//物件版本管理
versioning {
enabled = false
}
}
resource "google_storage_bucket_iam_binding" "binding" {
for_each = google_storage_bucket.frontend_bucket
bucket = each.value.name
role = "roles/storage.legacyObjectReader"
members = [
"allUsers",
]
}
ref.
- 讀取之前的設定
在建立private cluster的時候,就已經建好了vpc ,
相同的網路,我想在建立mssql 時使用,
使用data呼叫這個VPC。
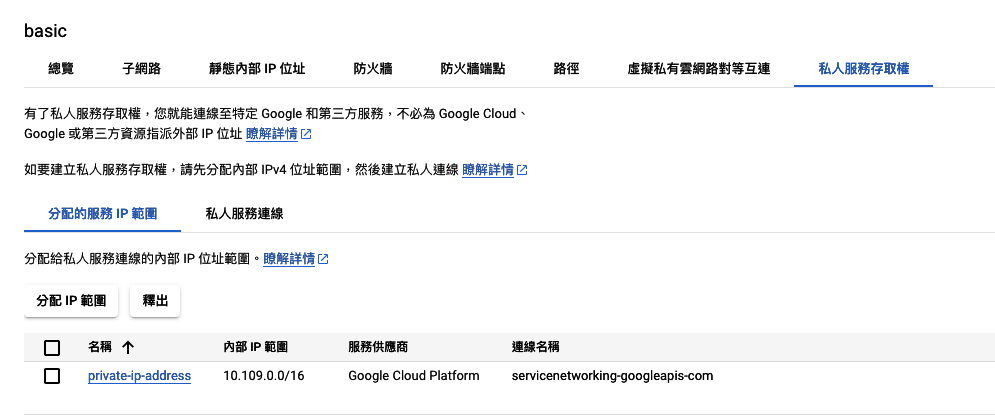
這個範例是拿來建立vpc裏面的私人服務連線的位置。
data "google_compute_network" "private-network" {
name = "basic"
}
resource "google_compute_global_address" "private_ip_address" {
depends_on = [ google_project_service.project ]
name = "private-ip-address"
purpose = "VPC_PEERING"
address_type = "INTERNAL"
prefix_length = 16
network = data.google_compute_network.private-network.id
}
resource "google_service_networking_connection" "private_vpc_connection" {
network = data.google_compute_network.private-network.id
service = "servicenetworking.googleapis.com"
reserved_peering_ranges = [google_compute_global_address.private_ip_address.name]
}
- 設定.gitignore
# Local .terraform directories
**/.terraform/*
# .tfstate files
*.tfstate
*.tfstate.*
# Crash log files
crash.log
crash.*.log
# Exclude all .tfvars files, which are likely to contain sensitive data, such as
# password, private keys, and other secrets. These should not be part of version
# control as they are data points which are potentially sensitive and subject
# to change depending on the environment.
# *.tfvars
# *.tfvars.json
# Ignore override files as they are usually used to override resources locally and so
# are not checked in
override.tf
override.tf.json
*_override.tf
*_override.tf.json
# Include override files you do wish to add to version control using negated pattern
# !example_override.tf
# Include tfplan files to ignore the plan output of command: terraform plan -out=tfplan
# example: *tfplan*
# Ignore CLI configuration files
.terraformrc
terraform.rc
ref. gitignore
結尾
基礎概念介紹